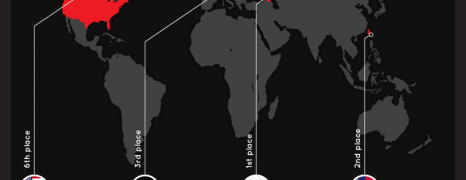
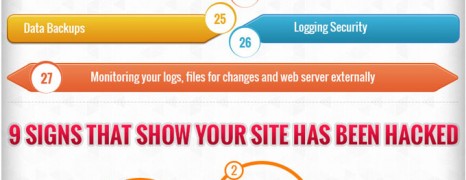
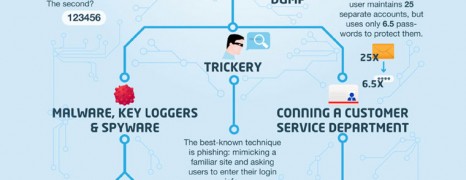
Learn about the basic types of internet crimes and relevant activities. Get an overall picture of cyber crime around the world and the costs involved.
eGov Security
visualized by: Symantec
Egov implementation is expanding year by year in developed countries. The question is how public sector’s IT departments can stem the increasing threat of cyber attacks, avoid the pain of data breach and defend their system’s security?
WordPress Security Threats
visualized by: Graphs.net
Though Wordpress has managed to enter the mainstream of web development and stride to the forefront of CMS, that doesn’t mean that it’s invulnerable. Here you see an overview of the most common vulnerabilities, security holes and hacking practices for wordpress based sites and blogs as well as some basic advice on how to “guard” a WP installation.
World Online
visualized by: nowsourcing.com
BestCommunicationsDegrees spotlights some of the most significant facts and milestones from the world’s recent history that signify the contribution of internet to our fast changing world.
Password Weakness
visualized by: BackgroundCheck.org
Internet has gone wild and according to experts, even the strongest password can be cracked depending on the time and effort a skilled hacker would put on. This report highlights the common password weaknesses and hacking methods and suggests some best practices to protect your online information until the coming of new age in authentication methods.
Password Security Statistics 2012
visualized by: Carousel30.com
How common is your password? See the facts for recent password hacks across popular sites like Linkedin and Yahoo. And let it be a motive to give up the silly 123456 that we all used in ancient digital times.
Facebook Twitter Privacy Protection
visualized by: Dr. Yaser Alosefer
Does sharing, socializing, surfing actually mean living in public? It seems true if you are not regularly updated with the latest privacy patterns released on Facebook, Twitter and other frequently used internet platforms. Learn how to protect yourself in simple steps. We say: “Thank you Dr. Yaser”.
File Sharing and Security
visualized by: IglooSoftware.com
Business users are demanding flexibility in data and information usage by utilizing cloud services. However IT people and businesses are vastly itching for confidentiality issues. Could these two forces be harmonically combined?
Generation Gap In Computer Security
visualized by: Check Point
The gap is everywhere! Digital media and social networks are vastly used by various age groups. Which one seems to be the most aware or less savvy as far the computer security and sensitive data protection?
Small Business Cyber Security
visualized by: VERACODE
Small business owners consider their property like needle in haystack for the aspiring hacker. Unfortunately cyber security proves to be conversely proportional to the business volume.
Linkedin Passwords L...
visualized by: Rapid 5
Bad passwords make bad passphrases and cracking algorithms have been accordingly set up for these cases. 6.46 million stolen Linkedin passwords